As Darktrace regularly detects crypto-mining attempts the moment they occur on a network we can estimate the cash flow stream a cyber-criminal earned on a laterally moving Monero-miner infection. An idea that was unfortunately found in a legitimate and popular browser-cryptocurrency mining service called Coinhive.
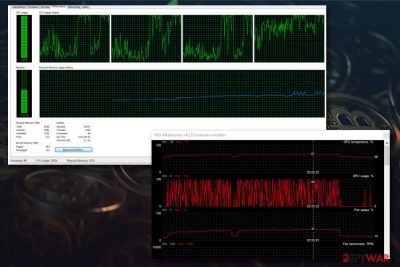
Bitcoin Virus Main Types Distribution Techniques And Removal Explained
Now security researchers at Malwarebytes are reporting that they have found evidence that millions of Android devices may have become part of the largest drive-by crypto-mining campaign targeted specifically at mobile devices.

Drive-by crypto mining malware detected. It is considered very dangerous as it has the ability to disable security features on the system and spread itself on the system without the users knowledge. However this is not considered to be as dangerous because it doesnt actually put any malicious files on your devices. The important thing is that they can bundle their power to mine crypto currency.
However many independently infected devices do not yet give cybercriminals much use. Researchers say that at least 60 million visits have been forcibly made to malicious Monero sites in. Some of these networks comprise several thousand computers and the profits that cybercriminals make are.
Use a PyRoMine Crypto-Mining Malware. For more information please see the following. It is called a drive-by crypto mining or a browser-based crypto mining.
Crypto Mining Malware has even been detected that is able to bypass antivirus programs. However drive-by activities have a shorter period of impact which means that mining activities will be interrupted once a user leaves the malicious website or chooses to close the. Dexphot is advanced but the cryptomining malware threat often takes second place to that of data breaches.
Researchers have discovered a strain of cryptocurrency-mining malware that abuses Windows Safe mode during attacks. A bot network is the ideal tool for this. PyRoMine Crypto-Mining Malware is a fresh malware that uses the EternalRomance tool and its main aim is Monero-mining or cryptocurrency mining.
The malware dubbed Crackonosh by researchers at Avast spreads through pirated. Therefore delete the PyRoMine Crypto-Mining Malware as soon as possible. However there are general indicators of how to tell if you have a Bitcoin Miner virus.
While there may not have been malicious intent in mind this JavaScript-based cryptocurrency mining. CoinDesk spoke with Michael Bentley head of Lookouts research and response team who said that the malware presents a new level of sophistication not normally seen in this type of cyberattack adding that the malware writer knew what he or she was doingThis week the app that contains cryptocurrency mining capabilities on the Google Play Store was discovered which was. Microsoft Defender Antivirus has detected malware or other potentially unwanted software.
Similar to malicious advertising exploits the scheme involves embedding a piece of JavaScript code into a Web page. Obvious signs of drive-by mining activity is a slow computer or a particularly warm device. The Varonis Security Research team recently investigated an ongoing cryptomining infection that had spread to nearly every device at a mid-size company.
Some of these networks comprise several thousand. This malware used in attacks such as WannaCry NotPetya and BadRabbit uses techniques such as encrypting hard drives with ransomware while also deploying Monero miners. A bot network is the ideal tool for this.
This means the Coinhive API has not been configured properly and mining activity is taking too many system resources. Interestingly cyber-criminals can deploy drive-by cryptocurrency mining to target a much wider audience compared to what they would typically achieve by delivering malware-based miners to machines. Still the act is perceived as unethical by most especially if the.
However many independently infected devices do not yet give cybercriminals much use. This is a JavaScript cryptocurrency miner with easy integration which can be embedded in websites by their administrators. Crypto Mining Malware has even been detected that is able to bypass antivirus programs.
The Cyber Threat Alliances CTAs The Illicit Cryptocurrency Mining Threat report describes PowerGhost first analyzed by Fortinet as stealthy malware that can avoid detection in a. After that it performs cryptocurrency mining on user machines that visit the page. The crypto mining tool runs in JavaScript and is loaded by infected websites or sometimes by websites where the owners deliberately decide.
If your computer started to act strangely its performance slowed up or dozens of spams pop-up on your screen the possibility of being infected with a virus is highly possible. Analysis of the collected malware samples revealed a new variant which the team dubbed Norman that uses various techniques to hide and avoid discovery. Crypto mining malware might be difficult to detect for those with poor skills in IT or cybersecurity.
Millions fall victim to drive-by cryptocurrency miner. The principle of the idea was as easy as pie to abuse this JavaScript in malware methods. It can quickly wear down a machine causes slowdowns and costs electricity.
An alternative cryptojacking approach is sometimes called drive-by cryptomining. Once in a computer system cryptomining malware can secretly use the devices resources to mine cryptocurrency sending the reward back to the cybercriminals. The important thing is that they can bundle their power to mine crypto currency.
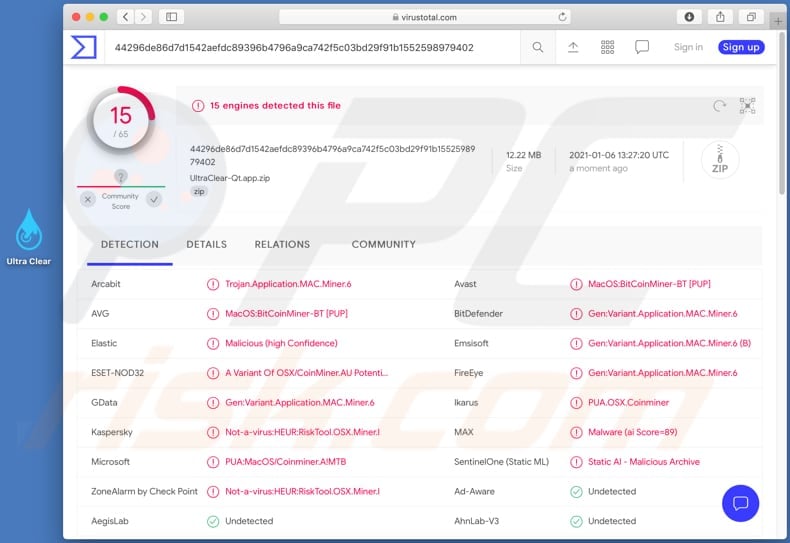
How To Get Rid Of Bitcoin Miner Malware Mac Virus Removal Guide Updated

Drive By Cryptomining Campaign Targets Millions Of Android Users Malwarebytes Labs Malwarebytes Labs

Combojack Malware Tries To Steal Your Cryptocurrency By Changing The Data In Your Clipboard Zdnet Cryptocurrency Blockchain Bitcoin
Https Www Researchsquare Com Article Rs 607598 Latest Pdf
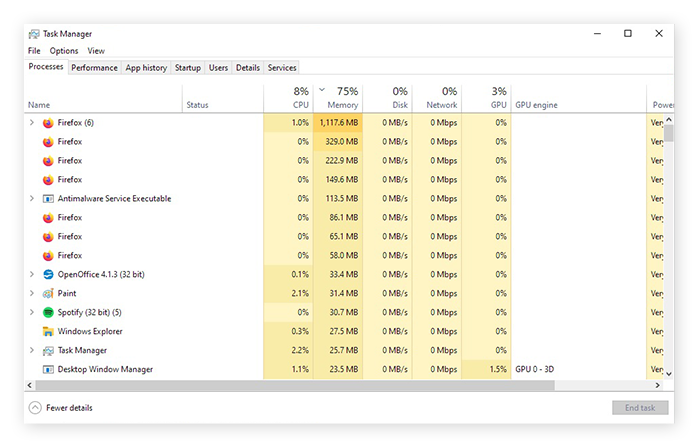
Cryptojacking And The Bitcoin Miner Virus Threat Avg
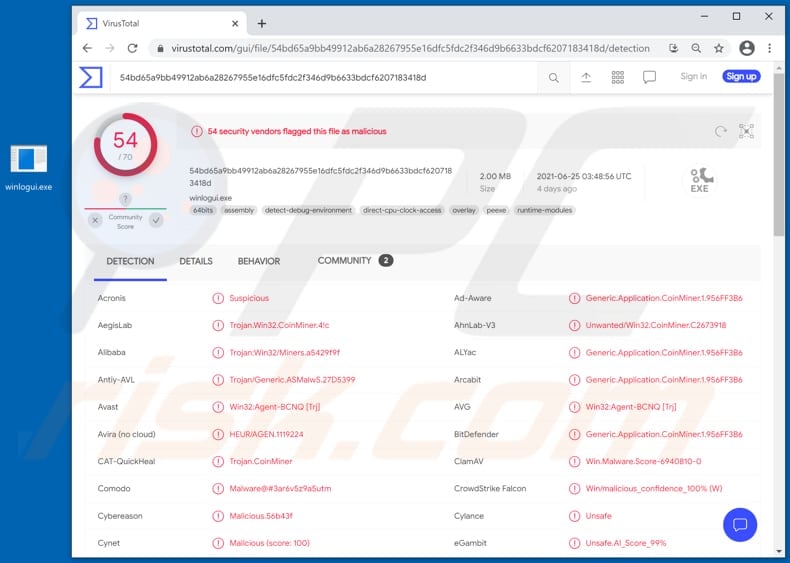
How To Remove Crackonosh Malware Virus Removal Instructions Updated

Sok Cryptojacking Malware Arxiv Vanity
Cryptojacking And The Bitcoin Miner Virus Threat Avg

Guiminer Exe Miner Trojan Removal Guide Free Fix Steps

Security 101 The Impact Of Cryptocurrency Mining Malware Noticias Sobre Seguranca Trend Micro Br

Bitcoin Miner Virus Trojan Bitcoinminer Detect And Remove

Drive By Cryptomining Campaign Targets Millions Of Android Users Malwarebytes Labs Malwarebytes Labs

Crypto Mining Malware Infected Cloud Storage Drive Manufacturer Cryptonetwork News Cnwn
Webmine Pro Javascript Miner Virus How To Detect Remove It

How To Detect And Remove The Bitcoin Miner Malware

Cryptomining Malware Computer Science Blog
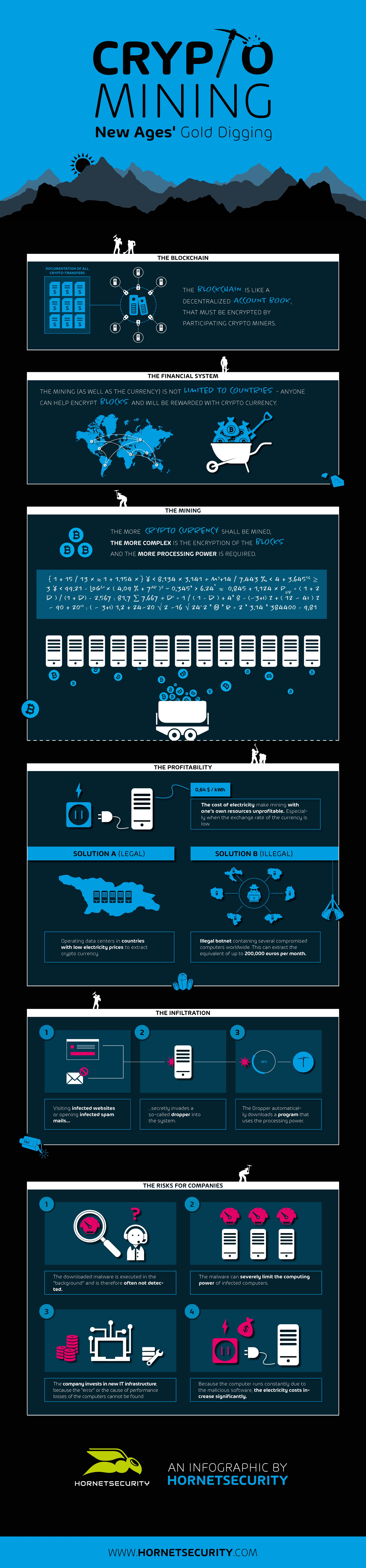
Crypto Mining How Do I Protect Myself From Illegal Attacks
Https Blogs Quickheal Com Detect Remove Bitcoin Miner Malware
