Researchers say that at least 60 million visits have been forcibly made to malicious Monero sites in. One of the major drawbacks of web-based cryptomining we mentioned in our paper was its ephemeral nature compared to persistent malware that can run a miner for as long as the computer remains infected.

Cryptocurrency Mining Malware And How To Stop It The Defence Works
But in general cryptojacking goes undetected much more often than other cybercrimes.

Malware drive-by crypto mining malware detected. If you are using Magento look for crypto mining malware in the database. Millions fall victim to drive-by cryptocurrency miner. After that it performs cryptocurrency mining on user machines that visit the page.
Examine the code and remove any JavaScript files being included there using the. While there may not have been malicious intent in mind this JavaScript-based cryptocurrency mining. Basically cryptocurrency mining malware stealthily hijacks devices like computers or phones and steals their resources for mining cryptocurrencies.
Fixing Crypto Mining Coinhive Malware for Magento. Cryptojacking attackers work surreptitiously. People may notice their computers overheating or working much more slowly.
Servers continue to get hacked with mining code and plugins get hijacked and affect hundreds or even thousands of sites at once. Similar to malicious advertising exploits the scheme involves embedding a piece of JavaScript code into a Web page. Trojans and other threats different from the malware showed fewer results in the samples infecting Apple computer systems.
Affected users are usually unaware when crypto mining malware runs complex calculations on their computers sucking up vast amounts of power. Once activated such a malicious file can affect individuals as much as large enterprises that rely their operations on networks of countless servers. Researchers have discovered a strain of cryptocurrency-mining malware that abuses Windows Safe mode during attacks.
Indeed when users close their browser the. The crypto mining tool runs in JavaScript and is loaded by infected websites or sometimes by websites where the owners deliberately decide. The malware dubbed Crackonosh by.
This means the Coinhive API has not been configured properly and mining activity is taking too many system resources. Open the core_config_data table table using a tool like phpMyAdmin and look for the value of designheadincludes. What does the crypto-jacking malware do.
Obvious signs of drive-by mining activity is a slow computer or a particularly warm device. An alternative cryptojacking approach is sometimes called drive-by cryptomining. More than 1305 malware samples of the crypto mining on Mac category were detected by AV-TEST.

The State Of Malicious Cryptomining Malwarebytes Labs Malwarebytes Labs
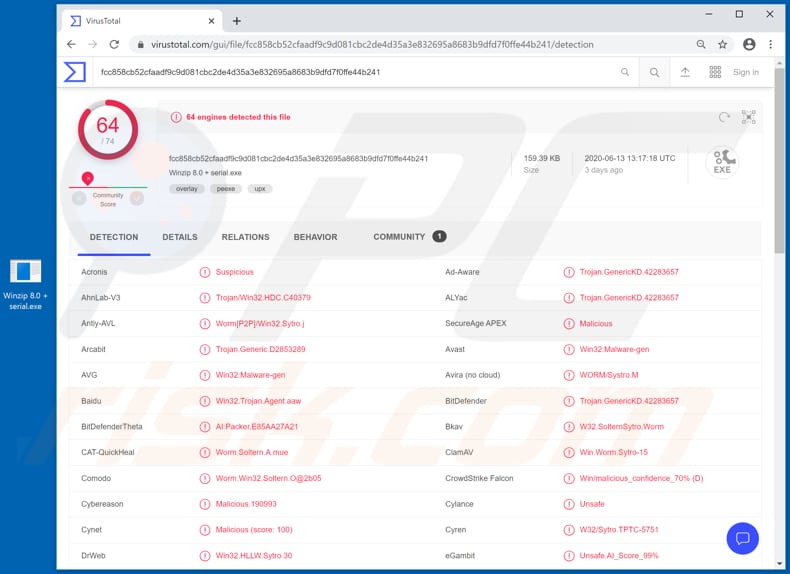
How To Remove Soltern Malware Virus Removal Instructions Updated

Combojack Malware Tries To Steal Your Cryptocurrency By Changing The Data In Your Clipboard Zdnet Cryptocurrency Blockchain Bitcoin
Https Blogs Quickheal Com Detect Remove Bitcoin Miner Malware

Security 101 The Impact Of Cryptocurrency Mining Malware Noticias Sobre Seguranca Trend Micro Br

Bitcoin Miner Virus Trojan Bitcoinminer Detect And Remove
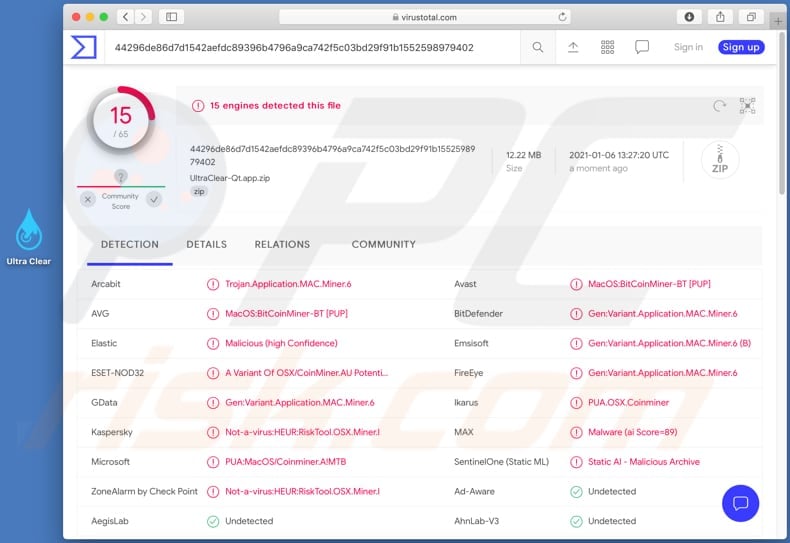
How To Get Rid Of Bitcoin Miner Malware Mac Virus Removal Guide Updated

Sok Cryptojacking Malware Arxiv Vanity

Cryptomining Malware Computer Science Blog
Cryptojacking And The Bitcoin Miner Virus Threat Avg

The State Of Malicious Cryptomining Malwarebytes Labs Malwarebytes Labs

What Is Cryptomining Malware Webopedia

The State Of Malicious Cryptomining Malwarebytes Labs Malwarebytes Labs
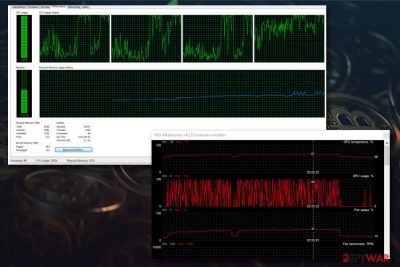
Bitcoin Virus Main Types Distribution Techniques And Removal Explained

Guiminer Exe Miner Trojan Removal Guide Free Fix Steps
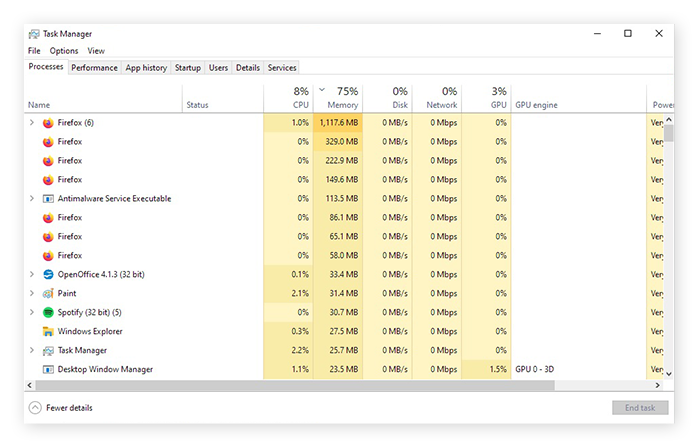
Cryptojacking And The Bitcoin Miner Virus Threat Avg

Crypto Mining Malware Infected Cloud Storage Drive Manufacturer Cryptonetwork News Cnwn

Drive By Cryptomining Campaign Targets Millions Of Android Users Malwarebytes Labs Malwarebytes Labs
