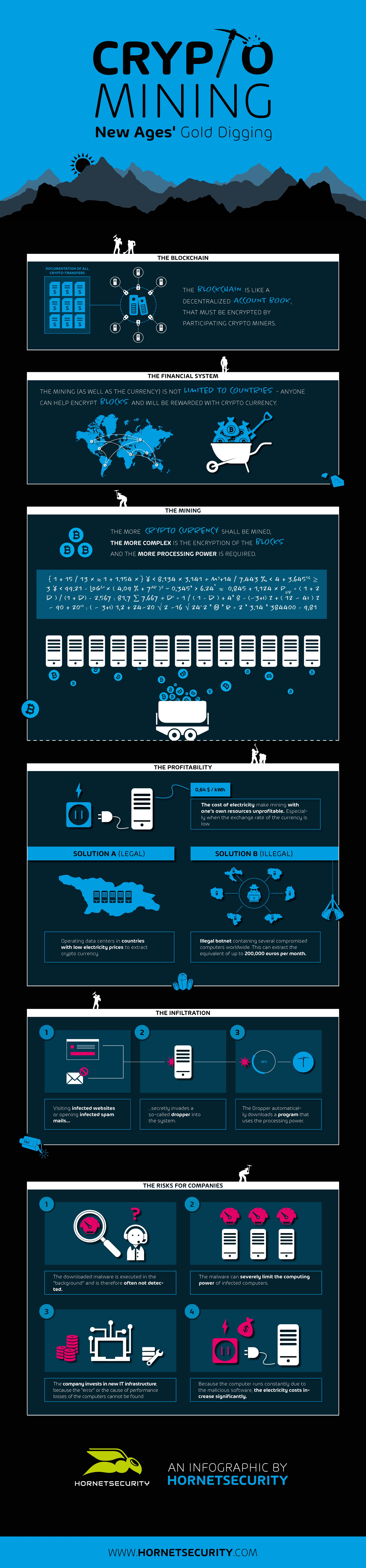
Script Jacking is malicious crypto mining that occurs when cybercriminals install hacking software on both work and personal computers laptops and mobile devices. Cryptocurrency is a digital form of exchange that makes use of a decentralized peer-to-peer network to produce record and send the coins over the chain.
What Are The Requirements For Mining Any Cryptocurrency Quora
By and large the environmental impacts of cryptocurrency mining have an effect on energy consumption.

How to detect crypto mining in your environment. Plus they also have to keep these systems cool which requires air conditioning in nearly all cases. How to prevent detect and recover from it Criminals are using ransomware-like tactics and poisoned websites to get your employees computers to mine cryptocurrencies. Once you choose the plan you need to pay the host perform the transaction and register your cryptocurrency wallet code.
The mining process involves miners competing to solve complex computing algorithms via cryptographic validation and the first one. Data centers pull a lot of power to keep the machines running. If the Bitcoin network has five computers mining transactions and then a bad actor joins five computers of their own the bad actor now has a 50 chance to.
The software uses your computers abilities and resources to mine crypto currencies and steal crypto wallets owned by. If you dont want to spend a dime and just get going ASAP you could give CPU mining. Through various attack vectors cyber attackers can turn compromised systems into a silent zombie army of cryptocurrency miners.
Miners perform this work because they can earn transaction fees paid by users for faster transaction processing. Thats why its vital to be able to effectively monitor systems for changes and determine if. The easiest way to tell if a site is legitimate is through a reverse image search.
More and more people are getting into cryptocurrency mining but how does this process affect the environment. All an attacker requires to start mining cryptocurrency in a serverless environment is a single vulnerable serverless function. Cryptojacking works in a fairly simple way but that doesnt mean its easy to detect or defend against.
However most crypto-mining occurs in areas with. Fortunately these attacks are easy to detect. These and many more similar questions will determine your best method for mining cryptocurrency.
These attacks often work by getting a victim to click a malicious link in an email that then loads crypto mining code onto their computer - or by infecting an online ad with JavaScript code that executes through a. If you would like to find out more about Falco. This is typically achieved with scripts that run behind the scenes on websites though its also possible to hijack machines and servers to run full-blown cryptocurrency mining software which is either installed by malware or by rogue employees.
If you want to build your rig then GPU is the way to go. Indeed anywhere that cryptocurrency mining is dependent on dirty energy sources such as coal the environmental impacts are markedly negative such as near the coal-fueled cryptocurrency mines in Mongolia. CPU mining is slow and tedious while ASIC mining could get very unpredictable especially as of late.
Process of cloud mining. First you would have to search for a cloud mining host online and see the different plans they offer and choose one as per your requirements. Generally speaking GPU and cloud mining seems to be the two big options that people love.
A pair of examples may help to illustrate how more computers on the network leads to more security. But even if we put aside these developments and focus strictly on the assertion that crypto is a threat to the planet it is important to distinguish the sources of energy that crypto miners use with data indicating that most of the electricity used for crypto mining comes from renewable sources. Unless you have advanced threat detection capabilities to detect crypto-mining activities on your endpoints in the cloud and on premises you might be unknowingly sharing your valuable computing resources with cryptomining criminals.
Cryptojacking works byyou guessed ithijacking other peoples processing power and using it to mine cryptocurrencies. The mining software listens for transactions broadcast through the peer-to-peer network and performs appropriate tasks to process and confirm these transactions. If the attacker can use remote code to gain access to one function.
Security tools like Falco can detect crypto mining processes and connections to mining pools and your monitoring solution can help you detect a rise in resource usage. A cryptocurrency transactions lifecycle Shortly after a users wallet broadcasts a transaction a nearby node will pick it up and add it to the Bitcoin mempool. The most effective way to detect cryptocurrency mining is on the endpoint directly he says.
How mining works. Mining of cryptocurrency provides a reward in exchange for useful services required to operate a secure payment network.

New Ai Based Algorithm To Detect Unauthorized Cryptocurrency Miners Algorithm Cryptocurrency Blockchain Technology

Home Twitter In 2021 Bitcoin Mining Bitcoin Mining Software What Is Bitcoin Mining
Crypto Mining How Do I Protect Myself From Illegal Attacks
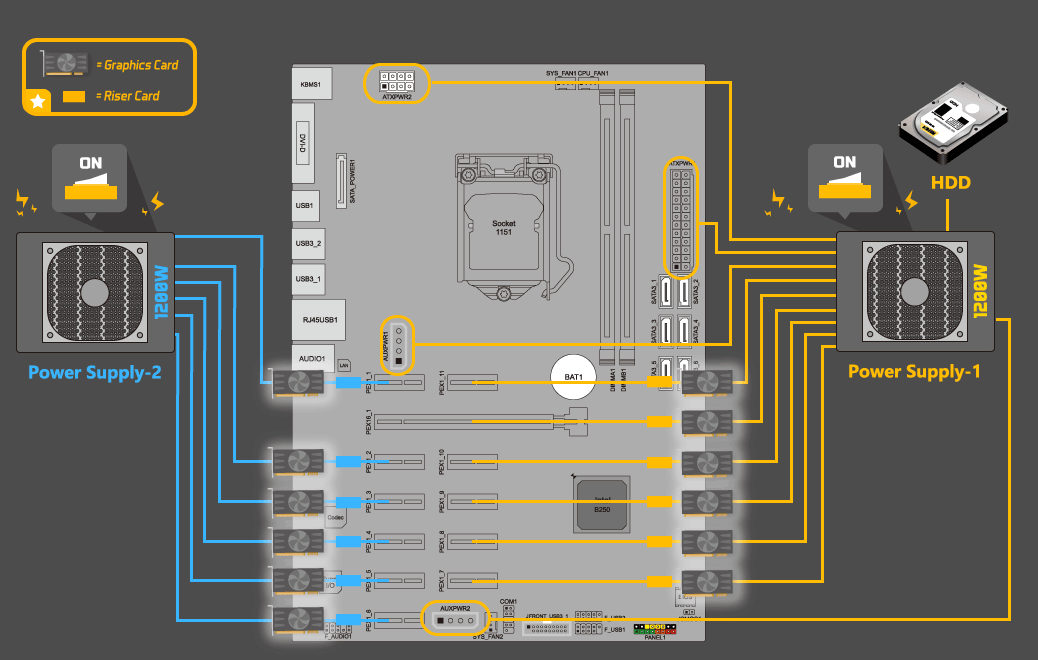
How To Set 12gpu Crypto Mining Rig For Bitcoin Biostar
Crypto Mining How Do I Protect Myself From Illegal Attacks

Cara Mengetahui Komputer Diam Diam Menambang Cryptocurrency

How To Set 12gpu Crypto Mining Rig For Bitcoin Biostar

How To Set 6gpu Crypto Mining Rig For Bitcoin Biostar

Crypto Mining How Do I Protect Myself From Illegal Attacks

Cryptocurrency Home Mining Rig Google Search Bitcoin Mining Bitcoin Mining Rigs Bitcoin

Daily The United Arab Emirates Need To Keep Up With Crypto To Support The Local Blockchain Industry Blockchain Market Environment Australia

How To Set 12gpu Crypto Mining Rig For Bitcoin Biostar

Crypto Mining How To Protect Your Systems From Illegal Mining

How To Block Cryptomining Scripts In Your Web Browser
Bitcoin Mine Discovered By Uk Police On Cannabis Farm Raid

Bitcoin Vs Gold In 2021 Bitcoin Cryptocurrency Gold

Exclusive Titan Now Rtx 3090 Monster 8gpu Rig Again The Etsy In 2021 Rigs Windows Software Mining

What Is Malicious Cryptocurrency Mining History And Prevention

