By Simona Ram. For example crypto mining traffic is periodic though malware writers will try to disguise the regular nature of the.

Pdf Detecting Cryptomining Malware A Deep Learning Approach For Static And Dynamic Analysis
An easy way to spot crypto mining malware is to go straight for the endpoint.
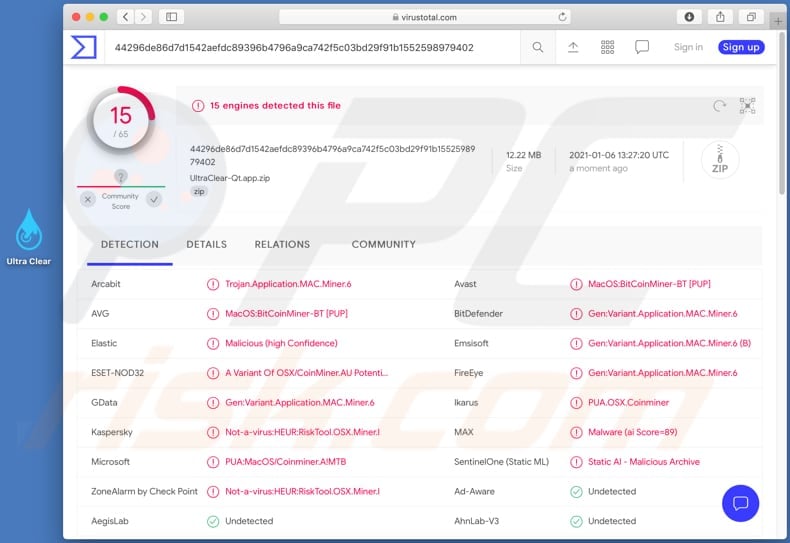
How to identify crypto mining malware. Slow performance lagging and overheating are warning signs of mining malware infection. What does the crypto-jacking malware do. Fixing Crypto Mining Coinhive Malware for Magento.
Cryptocurrency mining malware is typically a very stealthy malware that farms the resources on a system computers smartphones and other electronic devices connected to the internet to generate revenue for the cyber criminals controlling it. Moreover despite the decreased detection numbers cryptocurrency miner threats still remain the most detected malware. The difference between using bitcoin and using regular money is that bitcoins can be used without having to link any sort of real-world identity to it.
Illicit cryptocurrency mining may have simply reached a point of maturity. Open the core_config_data table table using a tool like phpMyAdmin and look for the value of designheadincludes. Thats why organizations should keep an eye on their systems to spot any apparent changes and determine whether or not they have an authorization.
Attackers inject a malicious code or script onto a website. Bitcoin Miner virus is general name malware that steals computers resources to generate cryptocurrency. There are thousands of factors that SecBI looks at Vaystikh says.
The script mines new cryptocurrencies on any computers that visit the. How to mitigate a cryptojacking incident. Once activated such a malicious file can affect individuals as much as large enterprises that rely their operations on networks of countless servers.
People fall prey by clicking a link in a phishing e-mail unintentionally loading crypto mining malware onto their computers. To prevent future attacks consider deploying an anti-cryptomining solution. Examine the code and remove any JavaScript files being included there using the.
There are several ways to identify the hidden crypto mining malware on our computer. Basically cryptocurrency mining malware stealthily hijacks devices like computers or phones and steals their resources for mining cryptocurrencies. What is Cryptocurrency Mining Malware.
These are the few ways to identify the cryptojacking malware on our computer. There are three ways that crypto mining malware can become embedded on a victims computer. A dangerous crypto mining malware mostly infects through downloads and browser-based attacks.
Bitcoin is a digital cash system. This article aims to help you detect and remove the newly emerged fileless bitcoin miner malware and protect your computer. We can either detect and identify that malware manually or by using the third-party antivirus or antimalware tools.
This type of malware mines cryptocurrencies on your system using your resources in such a way you wouldnt know. If you are using Magento look for crypto mining malware in the database. Web filtering tools and browser extensions need also to be kept up to date.
There are also ad-blocking and anti-cryptomining extensions for web browsers and endpoint and antivirus protection should be deployed that is capable of detecting cryptocurrency mining software. If youve experienced an in-browser JavaScript attack kill the browser window or tab running the script identify the website URL and update your companys web filter to block it. Threat actors are being more selective with their targets employing more sophisticated routines and refining attack techniques.

How To Get Rid Of Bitcoin Miner Malware Mac Virus Removal Guide Updated
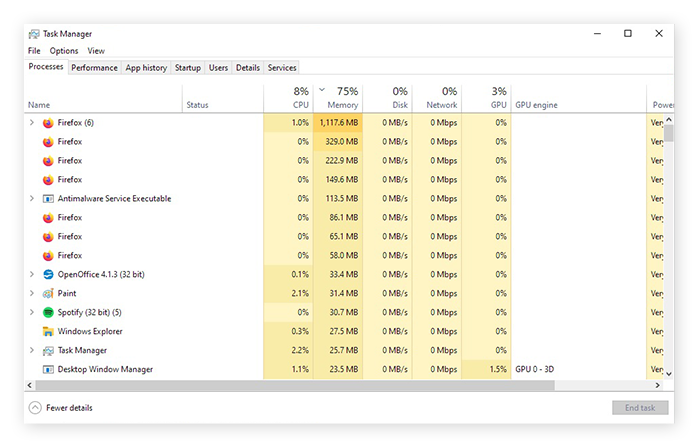
Cryptojacking And The Bitcoin Miner Virus Threat Avg

Xss From Alert 1 To Crypto Mining Malware
Https Blogs Quickheal Com Detect Remove Bitcoin Miner Malware

How To Detect And Remove Bitcoin Mining Malware

Att Lstm Model For Detecting Cryptomining Malware Download Scientific Diagram

Pdf Detecting Cryptomining Malware A Deep Learning Approach For Static And Dynamic Analysis
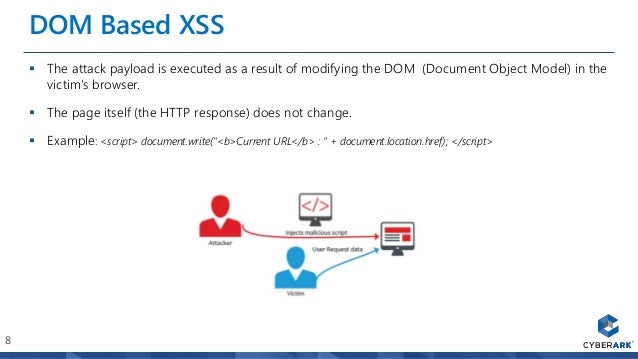
Xss From Alert 1 To Crypto Mining Malware
Cryptojacking And The Bitcoin Miner Virus Threat Avg

How To Remove Coinhive Miner Malware From Wordpress Site
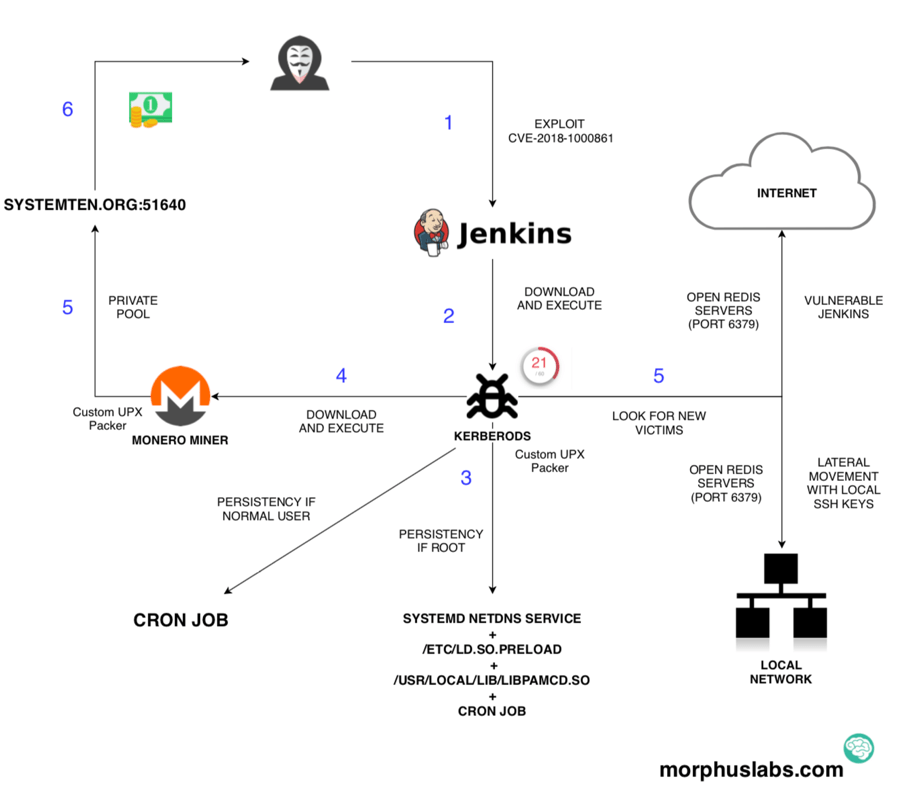
Jenkins Exploit Cryptocurrency Mining Malware Geko Cloud

Pdf Detecting Cryptomining Malware A Deep Learning Approach For Static And Dynamic Analysis

New Crypto Mining Malware Creates An Army Of Windows And Linux Bots News Block
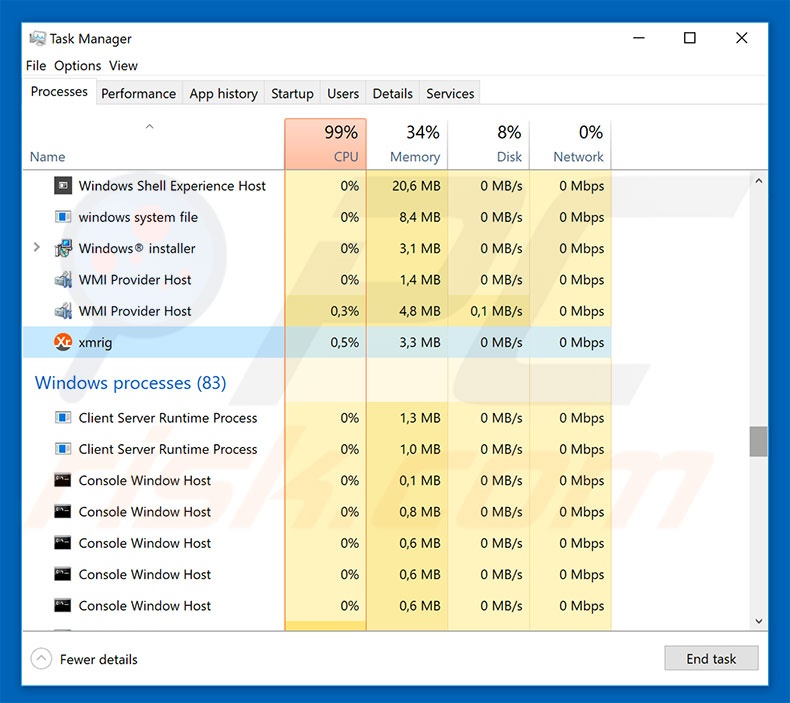
How To Remove Bitcoinminer Trojan Virus Removal Instructions Updated

Microsoft Defender Uses Intel Tdt Against Crypto Mining Malwaresecurity Affairs
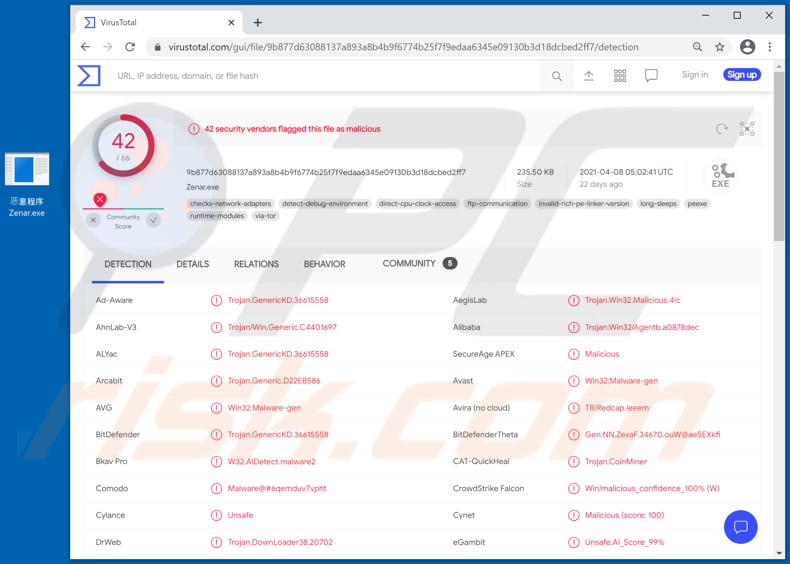
How To Remove Zenar Miner Virus Removal Instructions Updated
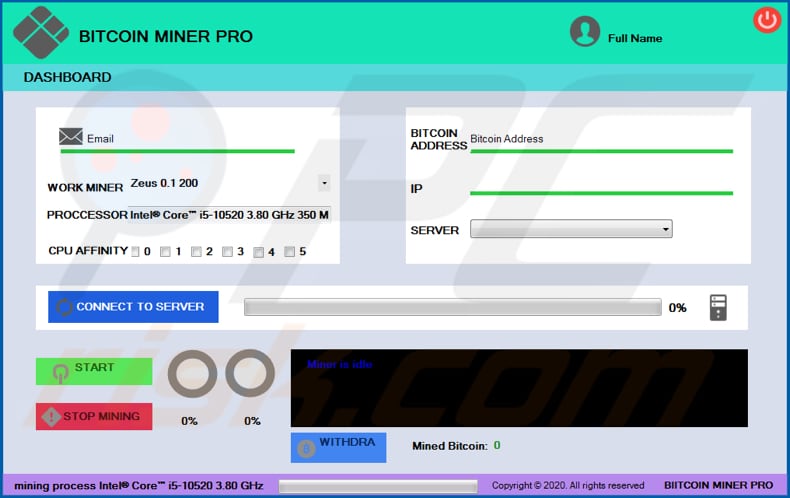
How To Remove Bitcoin Miner Scam Virus Removal Instructions Updated
What Is Crypto Mining Malware Cryptojacking Freewallet
