Wuapp was detected back in the middle of December 2017 and its primary goal on the victim computers was to drop multiple executable files of various processes then modify the Windows Registry Editor which results in the legitimate process Windows Update Service wuappexe to run in the background of the infected device. The practice of cryptomining or cryptocurrency mining involves adding various cryptocurrency transactions and evidence of mining work to the blockchain ledger.
 Pdf Detecting Cryptomining Malware A Deep Learning Approach For Static And Dynamic Analysis
Pdf Detecting Cryptomining Malware A Deep Learning Approach For Static And Dynamic Analysis
It has also been spread across Windows networks by exploiting the.

Crypto mining malware definition. This method uses malware specially designed for mining cryptocurrencies. The BitCoin miner malware are spread through numerous methods such as email attachments and embedded in compromised websites. Crypto mining using malware is a completely different matter.
This is a protocol within blockchain that helps different notes within a distributed network come to. Here are some real-world examples. Cryptojacking also called malicious cryptomining is an emerging online threat that hides on a computer or mobile device and uses the machines resources to mine forms of online money known as cryptocurrencies.
Many infections start with. Instead of delivering ransomware or a Trojan they are retooling that to deliver crypto-mining modules or components. Most cryptocurrencies are generated through a.
With the rise of digital currencies also known as cryptocurrencies criminals see a unique opportunity to infiltrate an organization and secretly mine for coins by reconfiguring malware. All this takes place without their owners suspecting a thing. The cybercriminals use different ways to smuggle it onto the computers of their victims.
Basically cryptocurrency mining malware stealthily hijacks devices like computers or phones and steals their resources for mining cryptocurrencies. Cryptomining malware or cryptocurrency mining malware or simply cryptojacking is a relatively new term that refers to software programs and malware components developed to take over a computers resources and use them for cryptocurrency mining without a users explicit permission. This malware is also found embedded in Trojan Horse viruses.
Once activated such a malicious file can affect individuals as much as large enterprises that rely. In digital currencies like Bitcoin the verification process is known as mining and it can be financially. Email messages with.
The most popular method of distribution is via infected websites. To mine any cryptocurrency you must be able to communicate to receive new hashes and. For example Coinhive the cryptocurrency mining service is often described as malware as a result of the tendency of the computer code.
Cryptomining malware is malicious code that takes over a computing devices resources so an attacker can use the devices processing power to track and verify cryptocurrency transactions in a distributed ledger. 1122018 Sustained mining could break your PCs hardware. 3232021 Illicit cryptomining is when malicious parties try to surreptitiously mine for cryptocurrency using the computing power of unsuspecting victims.
3292020 A typical Crypto malware is a malware code piggyback on popular apps which sneakily uses the processing power of thousands or millions of computing devices globally. All cryptojacking malware has one common aspect Vaystikh says. 1192021 Mining in the crypto world is the process of keeping blockchain data in check.
Recently Youtube witnessed another case of crypto jacking which was resolved by Google. It involves hard work done by computers and results in a. As a miner works to generate the block contents and algorithmic outputs that make up new blockchain transactions they are said to be creating a new coin of a particular kind in the blockchain.
How coin miners work. How is the BitCoin Miner Malware Spread. 7212020 Wuappexe Monero Coin Mining Malware.
Cryptocurrency mining or cryptomining is a process in which transactions for various forms of cryptocurrency are verified and added to the blockchain digital ledger. 342021 Browser mining is becoming an increasingly common practice. 10162020 In crypto mining the nonce gets added to the hash in each block of the blockchain and is the number that the miners are solving for.
 What Is Cryptomining Malware Webopedia
What Is Cryptomining Malware Webopedia
 Brutal Crypto Mining Malware Winstarnssmminer Crashes Your Pc
Brutal Crypto Mining Malware Winstarnssmminer Crashes Your Pc
 What Is Crypto Mining How Cryptocurrency Mining Works Infosec Insights
What Is Crypto Mining How Cryptocurrency Mining Works Infosec Insights
 Pdf Detecting Cryptomining Malware A Deep Learning Approach For Static And Dynamic Analysis
Pdf Detecting Cryptomining Malware A Deep Learning Approach For Static And Dynamic Analysis
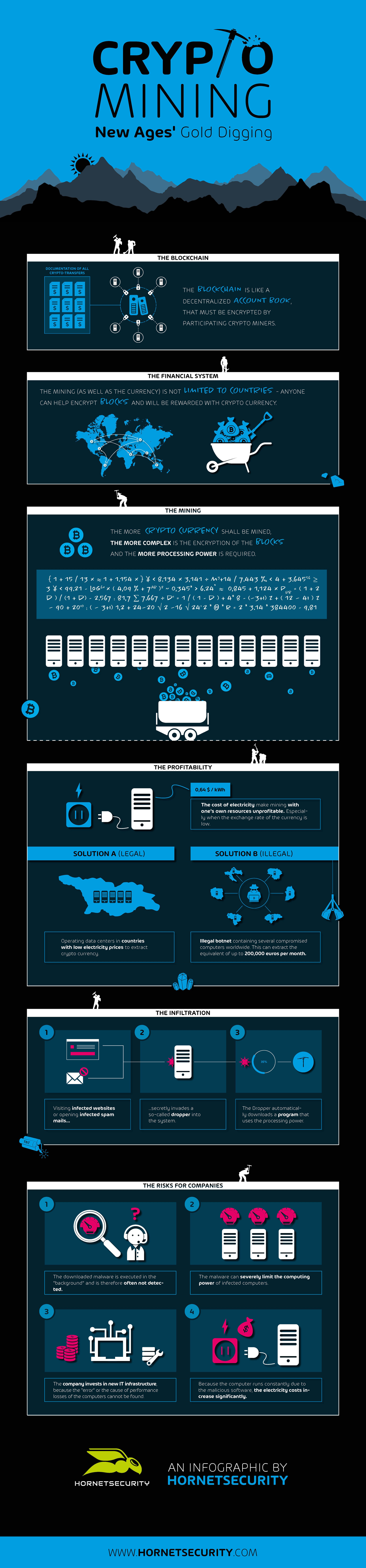 Crypto Mining How Do I Protect Myself From Illegal Attacks
Crypto Mining How Do I Protect Myself From Illegal Attacks
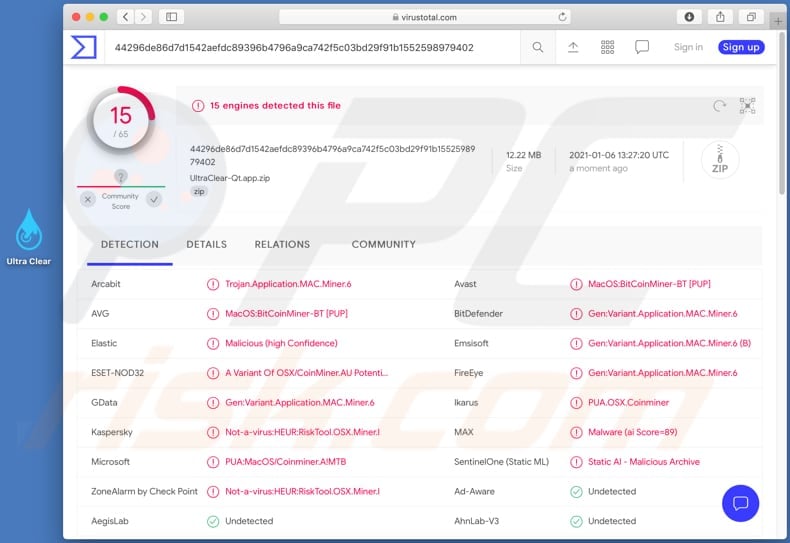 How To Get Rid Of Bitcoin Miner Malware Mac Virus Removal Guide Updated
How To Get Rid Of Bitcoin Miner Malware Mac Virus Removal Guide Updated
:max_bytes(150000):strip_icc()/cryptocurrency_mining_farm-5bfc31a546e0fb00517d0bd2.jpg) Illicit Cryptomining Definition
Illicit Cryptomining Definition
 What Is Malicious Cryptocurrency Mining History And Prevention
What Is Malicious Cryptocurrency Mining History And Prevention
 Pdf Detecting Cryptomining Malware A Deep Learning Approach For Static And Dynamic Analysis
Pdf Detecting Cryptomining Malware A Deep Learning Approach For Static And Dynamic Analysis
 What Is Crypto Mining How Cryptocurrency Mining Works Infosec Insights
What Is Crypto Mining How Cryptocurrency Mining Works Infosec Insights
 A Primer On Cryptocurrency Mining Malware Future Of Sourcing
A Primer On Cryptocurrency Mining Malware Future Of Sourcing
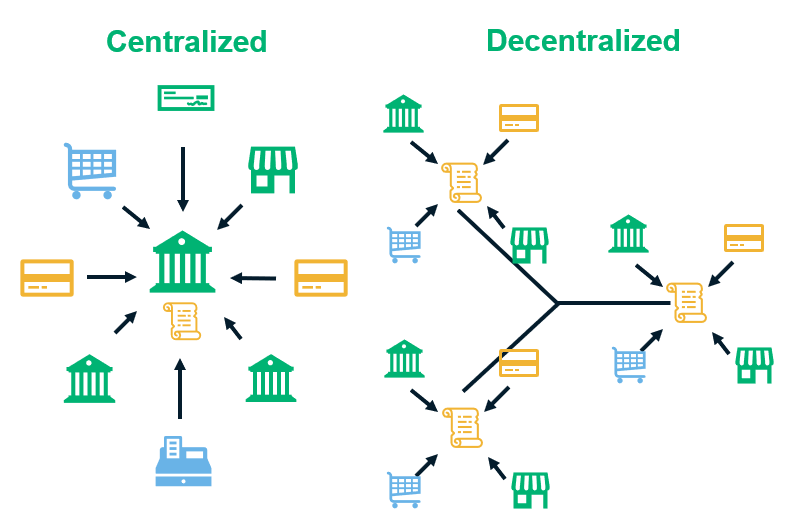 What Is Crypto Mining How Cryptocurrency Mining Works Infosec Insights
What Is Crypto Mining How Cryptocurrency Mining Works Infosec Insights
 Crypto Mining Malware Don T Be The Next Victim Protect Systems
Crypto Mining Malware Don T Be The Next Victim Protect Systems
 Cryptomining Malware Cryptojacking Definition Protection Eset
Cryptomining Malware Cryptojacking Definition Protection Eset
 How To Get Rid Of Bitcoin Miner Malware Mac Virus Removal Guide Updated
How To Get Rid Of Bitcoin Miner Malware Mac Virus Removal Guide Updated
 Pdf Detecting Cryptomining Malware A Deep Learning Approach For Static And Dynamic Analysis
Pdf Detecting Cryptomining Malware A Deep Learning Approach For Static And Dynamic Analysis
 Cryptomining Malware Cryptojacking Definition Protection Eset
Cryptomining Malware Cryptojacking Definition Protection Eset
 What Is Malicious Cryptocurrency Mining History And Prevention
What Is Malicious Cryptocurrency Mining History And Prevention